I knew I’d be facing some tough obstacles when starting my niche website. However, I expected to encounter the obvious difficulties that come with growing a website. Those being SEO, traffic, link building, social media and everything else that requires a great amount of effort. I never thought I’d be hit with such a nasty malware attack.
When I first found out about the hack, it had probably been a month since spammers started taking advantage of my server. I take great pride in security and have firewalls and scanners both on the site level and server level. Still, these hackers managed to find a way in and I think they may have exploited some plugin vulnerabilities. I believe it might’ve been related to the massive malware campaign reported here. Although, I don’t use any of the plugins listed in the article, given the recent WordPress update that fixed a bunch of security issues, I’m fairly certain a similar exploit was employed.
What could’ve turned a good month into a great one has resulted in many hours of investigating and troubleshooting. I’ll have a lot more details about what happened, the steps I’ve taken to clean the hack, and some valuable lessons learned. First things first, however. Let’s get to the good portion of this post and go over earnings and numbers!
Current Metrics and Statistics of my Niche Website
Trust/Citation Flow and Domain/Page Authority
ROOT DOMAIN
TF: 12
CF: 54
HOME PAGE
DA: 26
PA: 28
Observations
Add 4 more points to the citation flow score over the last month! I’d really like to see the trust flow go up too as I worry about such a large separation. A smaller increase in page authority (1 point) was also observed. Neither of these increases comes as a surprise since the backlinks I acquired were probably still being tallied at the time.
It’d really be great if some natural backlinks started popping up. I’ve poured my heart and soul into creating meaningful and unique content. Although, I do think people are starting to recognize the authority that Kettlebell Krusher is building. Lately, I’ve been getting more inquiries from people wanting to provide me helpful content. Obviously, they want to use my site for their own backlink purposes. I suppose I should be flattered and realize that the metrics are improving outside of my own observations.
Keyword Rankings
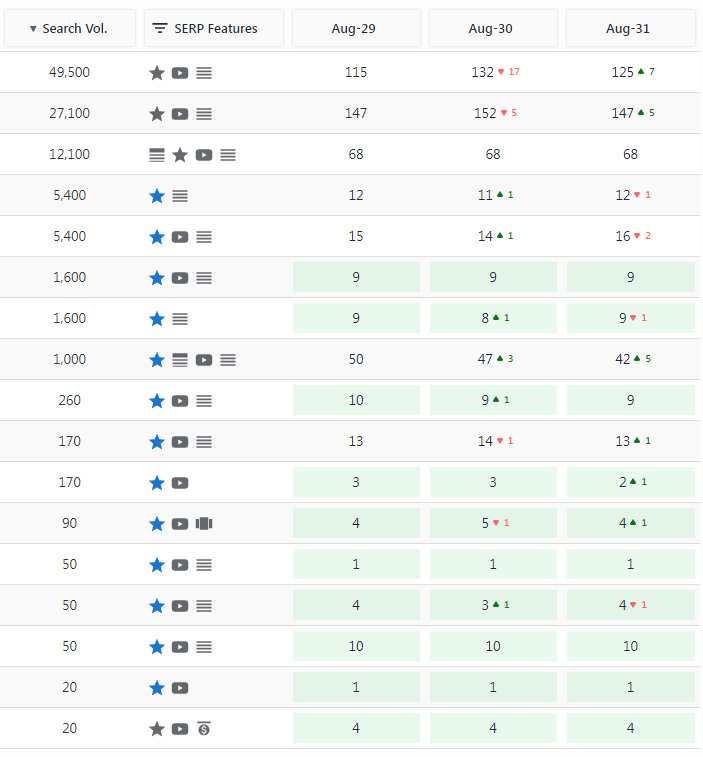
The 1,200 and 1,000 volume keywords enter the top 100, otherwise, not much movement.
Observations
Keyword rankings remained relatively stable in positions close to the prior month. Normally, I’d be a little disappointed but I’m very happy that the malware attack didn’t tank those rankings. I believe Google has gotten a handle at virtually eliminating negative SEO. If this was 5 or 10 years ago, I doubt I’d be so lucky.
I did add one new keyword to this report, the 170 volume that is in the 13th position. This is an extension of the two-word 1,000 volume keyword which adds another word at the end of that phrase. Seeing the progress of these two keyword phrases is very exciting considering the amount of time I spent creating the targeted page. In fact, I’ll be editing that page to cross-link with another product for the chance at even higher earnings.
Amazon Affiliate Earnings
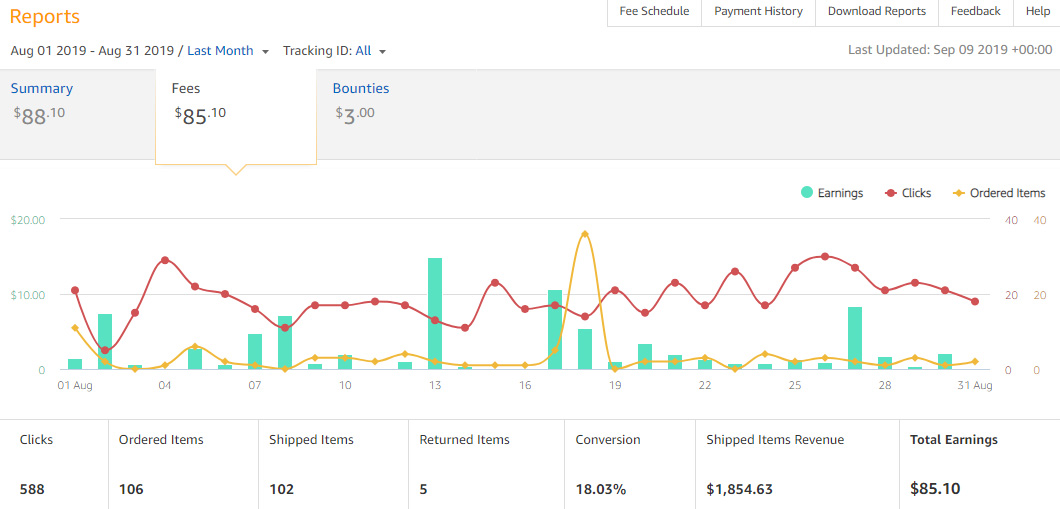
Roughly $16 increase from July. Hopefully this upward trend is here to stay!
Observations
Well, would you look at that, another bounty commission! It’s only $3 and I have no idea what it was for (special promo??) but it’s a nice unexpected bonus. Everything is up for this month in the stat column. Yes, that includes returns. Usually, 5 returns would be considered horrible but I’m pretty sure each was for low-priced items and didn’t take a large chunk out of the earnings.
Clicks increased by 59 from July and ordered items are also way up. That looks a little too high for ordered items wouldn’t you say? There’s a reason for that. For the first time ever I saw someone purchase an entire grocery list of items. Food, produce, household items, etc. The list was so large for that day that I actually had a next button for ordered items to view another page. That’s great and all but the commission rate on that $150 worth of groceries was pretty low. I think I got maybe $5 off of that.
For such limited traffic, these are great numbers. And that’s what it is – a numbers game. If I can get more traffic, I expect the conversion rate to remain the same. As far as the international earnings from Amazon, not much to report. Although, the UK is still my biggest secondary market and I try to keep that in mind in my articles (such as listing the kettlebell weights in both pounds and kilograms).
Google Analytics Traffic
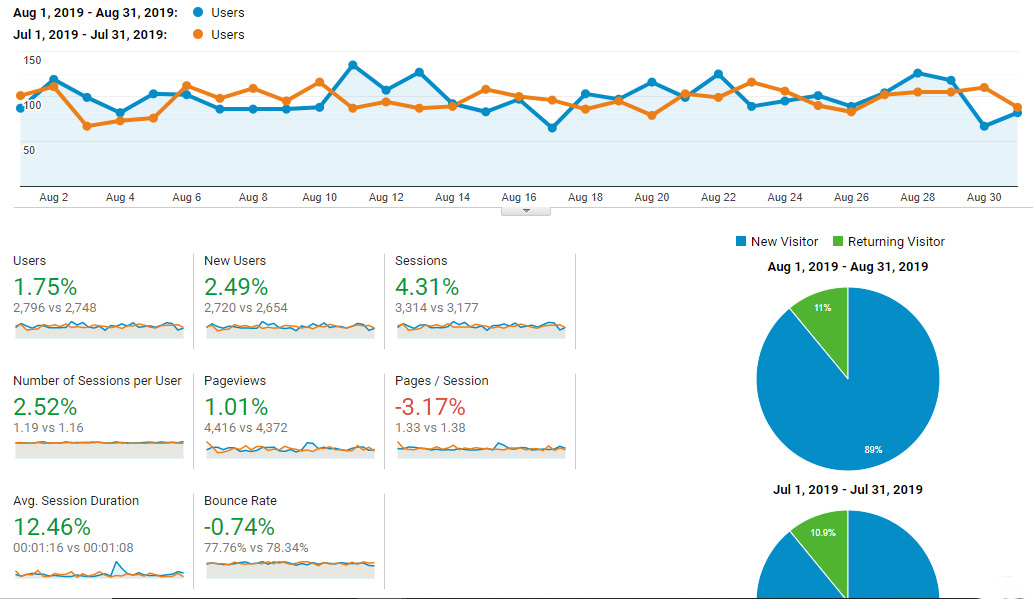
Slight increases across the board. Still waiting for that huge spike.
Observations
New users for the month of August edged out the previous month by approximately 70. That’s not much cause for celebration but at least it’s not a decrease. Granted, the overwhelming majority of traffic is coming from Google. I hate relying so heavily on one source for visitors, but that’s just the way it is.
Ideally, I’d love to be generating meaningful traffic from social media. Every day I might get anywhere from 1-5 visitors from Pinterest. On Instagram, I’m lucky to get several clicks a month. It does seem like both Pinterest and Instagram give a slight boost to new accounts. Perhaps to encourage them to stay consistent and engaged on the platform.
I haven’t had a viral pin in a while and it’s also much harder to get Instagram followers these days. Still, I’m counting on the long game in the hopes that continuing to promote the Kettlebell Krusher brand on these two social media sites will eventually pay off. Both in the eyes of Google and for referral traffic.
The Malware/Hack Incident
Normally, this section is where I discuss any notable accomplishments for the month. In August, I wrote several pages and posts targeting multiple keyword clusters. I also worked really hard promoting these pieces by creating some videos and relevant social media posts. However, in terms of organic exposure, it was pretty much all for nothing. At least for the moment.
Even though the hack happened over a month ago, there were some warning signs that I missed. Below, I’ll be providing a rough timeline of events that should have clued me in that something was seriously wrong. Hopefully, this information will help others in minimizing the damage and impact these hacks have.
Malware Timeline
Beginning of August
I noticed that Bing had completely removed my website and all of its pages from their index. I really wish I would have compared with Google, however, I assumed it was a glitch. So I contacted Bing support and they did acknowledge there was a problem. Although, they didn’t elaborate on the issue and were either unaware or neglectful in informing me of the nature of the removal.
The ticket that I opened was forwarded to an agent who then forwarded it to a supervisor. After a few days, I got a message saying that my site would begin reindexing and that it would take some time for all of the pages to reappear. I thought it was strange but chalked it up to a bug and figured these things happen.
My pages did start to reappear in Bing’s index and I thought that it was solved. Flash-forward to the end of August (after I discovered the hack) and again I noticed my website was completely deindexed. In fact, if you do a “site:kettlebellkrusher.com” as of today (9/12/19) in Bing search the message Some results have been removed is displayed. Some results? More like all!
I haven’t contacted them again as I know I’ve eliminated the effects of the Malware but am not 100% certain that the backdoor or regeneration of malware files process has been stopped. Honestly, Bing accounts for less than 5% of monthly traffic so it’s not like the site is suffering much. However, I still want to capture every slice of the pie as they say and even if one of those Bing visitors converts, that’s money lost.
What’s really frustrating is that both Bing and Google Webmaster Tools have security tabs with malware notices. I never got any warnings or errors from either of them. You’d figure that given the nature of this malware (pharma spam) that any massive indexation of the content of this type would trigger a flag. Nope, everything is “OK” according to them.
Middle of August
At this point, I noticed another serious problem. My newly written content was being indexed but not searchable. This means that even copying large blocks of text and adding “Kettlebell Krusher” would bring up other past articles but not the new ones. This issue is still ongoing. Again, I figured it was a Googlebot issue as I’ve read that they’ve been having coverage issues throughout the year sporadically.
This is perhaps the 2nd most upsetting part of the malware problem I’m dealing with. The first being cleanup and removal. I can’t tell you how aggravating it is to spend hours upon hours writing content only to have it sit somewhere in Google’s nothingness. All that effort spent incorporating multiple keywords in the several posts of 1000+, 2000+, and 3000+ word articles have yet to be rewarded.
End of August
The hack is finally discovered. I happened to be clicking around a certain section in Google Webmaster tools and noticed something extremely unsettling. In the Coverage section the indexed pages jumped from a couple hundred to 60,000. It looks like a wall. The excluded list is several times larger which is equally alarming.
Seeing this spike in coverage finally prompted me to do a “site:kettlebellkrusher.com” in Google where I was horrified to see those 60,000 results listed. All of those pharma pages are gibberish non-sense which some of them were redirected to a Canadian online pharmacy. I suspect that the intent was to boost the authority of this website or an attempt to run a negative SEO campaign and destroy the reputation of my website. Why else would pages with pharma terms be thrown together with no cohesion? You can see what Google has listed in their coverage as of today in the screenshot below.
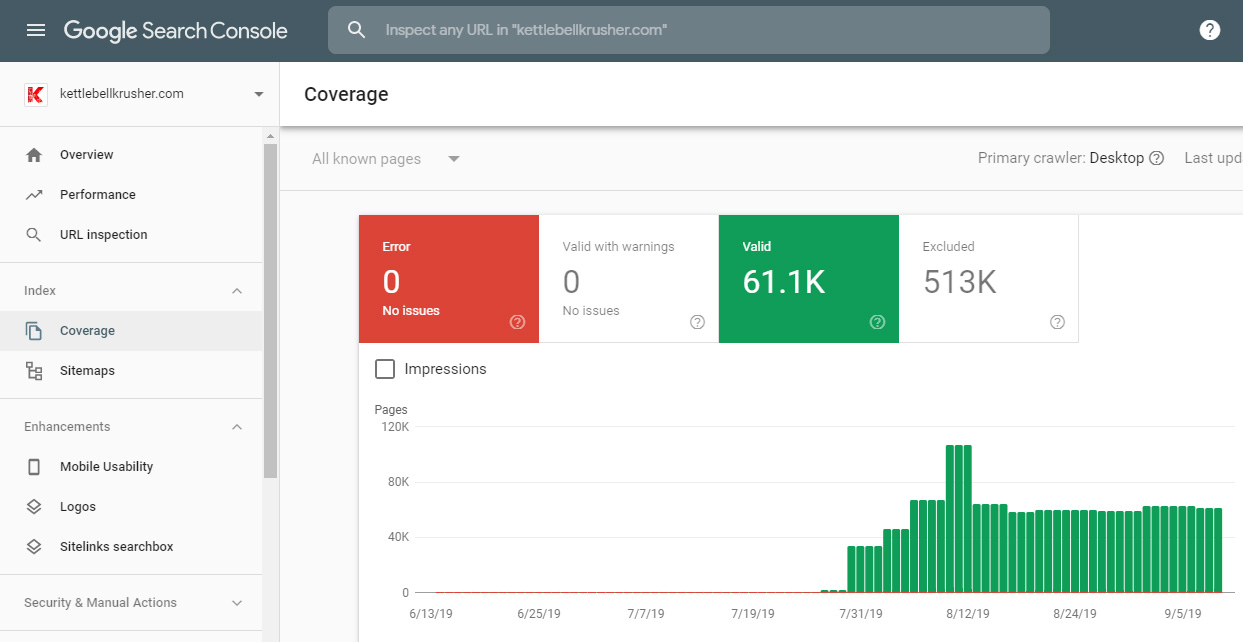
Shouldn’t going from a couple hundred pages to thousands trigger a warning?!?
Malware Cleanup and Removal
So here comes the fun part. Dealing with this nightmare and trying to rid not just my website, but my server of this infection. None of my firewall and security scanners picked up on any malware issues. Instead, I had to rely on new anti-malware plugins for WHM/cPanel and WordPress.
For WordPress, I’ve been a huge fan of Eli’s Anti-Malware Security and Brute-Force Firewall and WordFence. Although I consider Eli’s plugin to be more of a fixer of sorts than something to prevent an attack. WordFence, isn’t something I’ve installed on each of my sites because I thought I was covered adequately with ConfigServer Firewall for WHM and other server plugins.
Running scans on both discovered that several core files in the wp-includes directory were modified with malicious code. On top of that, a couple of new files were also present that aren’t packaged with WordPress in the includes directory. Both were named so as to not stand out. One was labeled wp-class-xml.php and the other had ssl in the filename.
This malware acted as a worm of sorts. It went into the many website directories on my server (both active and websites that were no longer live) and infected/generated the same files. Any attempt to remove these files would just cause them to be regenerated at a later time. Clearly, I had my hands full.
Locating the Source of the Spam Posts
The wp-class-xml.php and other non-core file were encoded with string characters, presumably responsible for regenerating the modified core files. I looked everywhere else for a backdoor. No rogue administrator accounts and not even a trace of the pharma spam posts in any of my MySQL databases. So how the hell was this happening?
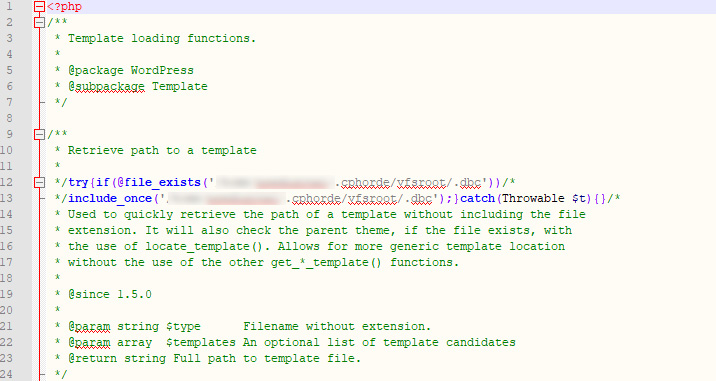
All of the infected core files had these two lines of code.
It turns out that each and every of the modified core files had a line of code pointing to one file in a remote directory of the server. I compared this directory with another account on my server which had not been hacked. What I discovered is that no files were in the good directory. The hacked one had a few files that were labeled .dbc .dbb, and similar.
After looking at the contents of these files I was unable to determine what instructions were created due to heavy encoding. One thing is for certain, these files were acting as a proxy of sorts. Most likely receiving the content from the hacker’s server and transmitting to all infected sites on my server. In a way, it’s a brilliant method of hiding this junk content.
After deleting these files and keeping a watchful eye, I saw that they were also regenerating. I needed to put a stop to this one way or another so since this directory was empty I simply changed all the permissions to read-only across the board (444). That prevents any files from being written. And you know what? No more regeneration and the spam link has been severed.
How This Malware Evades Detection
I think when I was originally clicking on these spam links indexed in Google something wasn’t working as intended by the hacker. I was getting redirected to that Canadian pharmacy website. However, when I did the same in an incognito window, a 404 (file not found) error happened in every instance.
These bastards wanted me to believe that there wasn’t any issue at all. Or that it was removed. In actuality, this spam content was only intended to be visible for Googlebot. This way, they get the benefit of being indexed in Google while seemingly invisible to webmasters and actual visitors.
Luckily, there is a way to trick chrome into thinking the user agent is Googlebot. Right-clicking inspect on a page and then 3 dots at the top-right and finally navigating to More Tools > Network Conditions allows you to choose from multiple user agents. After selecting Googlebot, the curtain was pulled back and I saw the pharma gibberish that was indexed in Google.
When the link was severed, these pages became invisible. From what I read, this isn’t all that uncommon as there might be some javascript in my theme preventing it from displaying to my faux Googlebot agent. Obviously my regular content is indexed just fine so there is no worry.
Installing and Running New Server Malware Applications
To aid me in locating all of the infected files as well as discovering any ones that I missed, I installed two new plugins for Web Host Manager. Webdefender and cPMalScan. While Webdefender has the prettier interface, both of these plugins found several infected files that the other didn’t.
cPMalScan also has a WordPress plugin, but I figured it would be easier just to install it on the server level and do a wide scan. There were a lot of false positives from both scanners but that’s fine. I’d rather have that than a chance of missing even more infected files. Also, both of these programs were free either in a trial mode or limited functionality. I haven’t been hassled to upgrade, although, I think that they would absolutely be worth the few bucks a month cost.
I’m still in the process of keeping an eye on malware regeneration. I’ve checked cron files, and looked for other ways that would help the core files and malware files from being recreated. I’m not sure if I’ve found the source as I’ve been deleting like a madman but it’s been a couple of days since the last regeneration. I figure I’ll continue to run scans with both of these plugins every so often to ensure that no new files pop up.
Dealing with the Aftermath
So what to do about the thousands of spam URLS indexed? I did purchase a chrome extension from a bulk URL removal tool that is compatible with the Old Webmaster Tools in Google. It’s not perfect and ultimately, I decided I just need to wait for Googlebot to recognize the true 404 errors now and hope that it will slowly remove them from the index.
So far it seems to be working. Performing the site command from time to time I’ve seen the number of indexed pages drop from 60k to 15k, to 10k, and now to roughly 5k. Hopefully, another week or two and it will go back to the correct amount of pages.
Once that happens I’m crossing my fingers that the content I’ve worked so hard on will finally become searchable. Although the severing of the pharma link also presented another problem. All of the robots trying to crawl these websites have created a sort of DDoS effect. This was killing my server’s performance.
Imagine Google, Bing, Ahrefs, SEMrush, and other bots pounding your server every millisecond performing GET requests on those thousands of now missing pages. Well, you don’t have to imagine it as I have another lovely screenshot below.
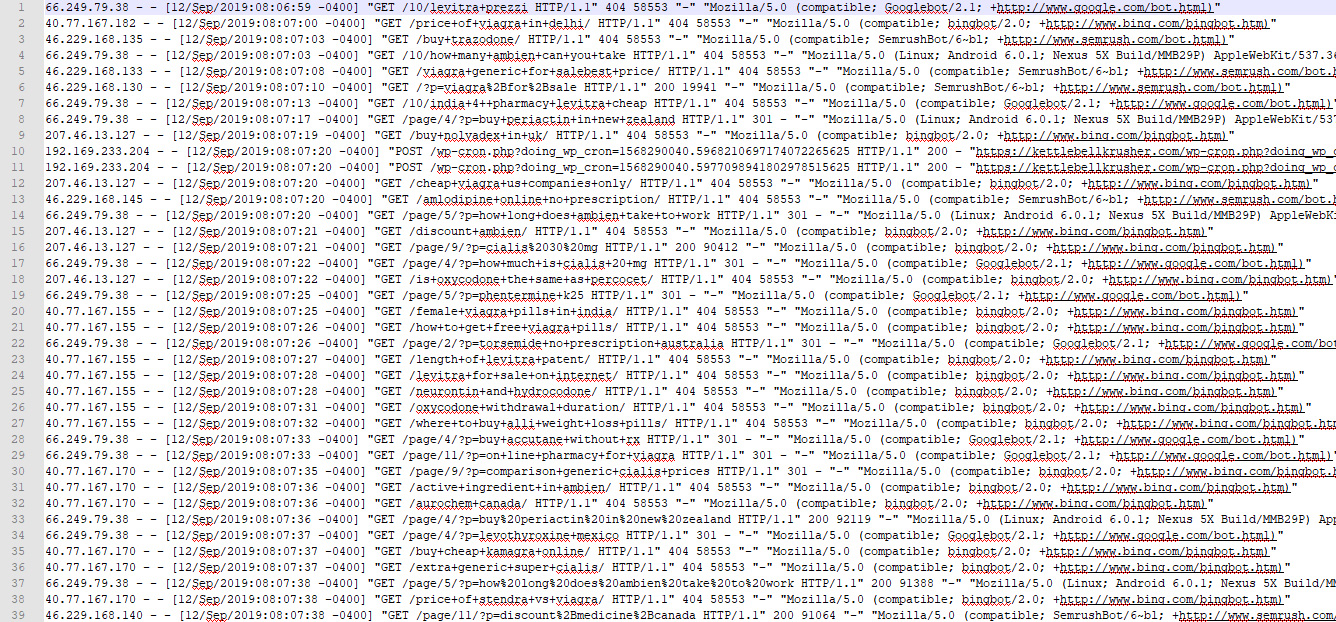
All of those pages being requested every millisecond!
The Effect on Server Performance
WHM features an indicator at the top right which computes the server load in one, five, and fifteen-minute averages. These numbers should be around 1 or so. Any larger than that means that the server is working harder than it should be.
Upon first removing the hack those numbers were in the 30’s! That’s a huge strain on the server. I’m surprised it didn’t crash. My solution was to check the raw access log of various sites and compile IP addresses of all the bots I could care less about.
Using ConfigServer’s firewall block list, I added the likes of SEMRush, Blexbot, Ahrefs, and several others to the banned list. This would block them from the server entirely. I didn’t want to block Googlebot for obvious reasons. Now the load averages hover around 2.5 to 5. Much more reasonable. I expect that should continue to go down as the 404 errors of these spam pages are respected.
Wrapping Up Part 14 Of My Niche Dreams
I wouldn’t wish this type of malware or hack on my worst enemy. It’s that awful. In fact, I’ll probably submit this blog post to various anti-malware companies for review. I’m not looking to get a mention or backlink, rather, I hope that my experience with this can help others avoid a similar fate.
Going back to the positive side of this post. It is nice to actually have an increase in earnings despite the malware. I’m going to continue to create unique content and build the authority of Kettlebell Krusher. I’m extremely grateful that none of my current keyword rankings were impacted. In time, I expect that my new content will rank and perform just as well.
Also, I’ve started making connections for affiliate programs outside of Amazon. I’ll be jumping back into the ClickBank fray by partnering with a trainer and promoting his amazing product. I was also just accepted into another affiliate program from a premier fitness company even though my requirements were a little shy of what they were looking for. Commissions for both of these platforms will be higher than what Amazon offers so there is a lot of potential to be had.
Some of you are probably wondering the fate of this blog series since Niche Site Project 4 has concluded. After some thinking, I’ve decided to continue on with it. For one, the few readers who’ve reached out to me have really been so kind in their comments and feedback. I really appreciate that. The other reasons are because this IS the only blogging I do on this site. I’m so devoted to Kettlebell Krusher that I no longer have the time or desire to blog elsewhere. Lastly, I still believe that I’ll eventually break through and make some significant earnings. I’d love for the ability to share that moment and encourage others not to give up on their affiliate dreams.


