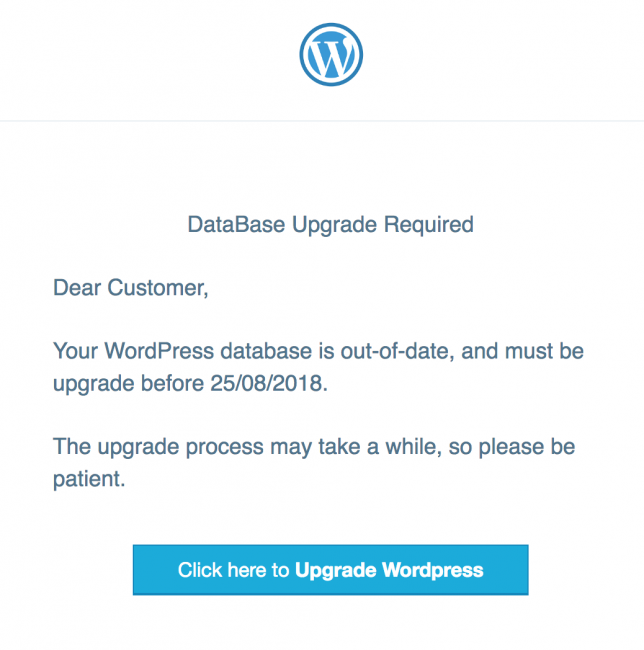
News Courtesy of Sucuri.net:
The email’s appearance resembles that of a legitimate WordPress update message, however the content includes typos and uses an older messaging style. Another suspicious item in the content is the deadline. WordPress wouldn’t define deadlines without a valid explanation, and hosting providers wouldn’t either (if you believed the email was from them). The use of timestamps in a European format may be another suspicious sign, especially for those residing in the US.
You should always exercise caution when receiving emails requiring you to submit information or perform an action. Usually, phishing emails are targeting bank accounts or other financial institutions. Even if an email looks legitimate, if there is doubt, always make a phone call to the institution that the email appears to be from.
A lot of the time, these phishing emails will be rife with spelling and grammar errors. In this case, “Upgrade” should have been written as “Upgraded”. However, the biggest gaffe with this phishing threat is on the fake database upgrade page. While it’s not uncommon to have to perform a database upgrade, it doesn’t make any sense to have to enter your website’s address. Upgrades are performed within the website’s domain and therefore that information is not necessary.
I have to wonder how successful this phishing campaign really is. WordPress administrators are typically a savvy bunch. We’re not talking about scams that go after the elderly. If this campaign is deployed on a massive scale then I suppose it is just a numbers game and some people will fall for it. For the most part, I’d wager that it is a huge waste of time on the part of the attackers.